In the present era, not only business but almost all the aspects of human life are driven by information. Hence, it has become imperative to protect useful information from malicious activities such as attacks. Let us consider the types of attacks to which information is typically subjected to.
Attacks are typically categorized based on the action performed by the attacker. An attack, thus, can be passive or active.
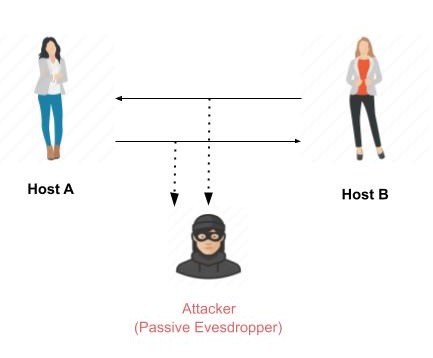
Passive Attacks
The main goal of a passive attack is to obtain unauthorized access to the information. For example, actions such as intercepting and eavesdropping on the communication channel can be regarded as passive attack.
These actions are passive in nature, as they neither affect information nor disrupt the communication channel. A passive attack is often seen as stealinginformation. The only difference in stealing physical goods and stealing information is that theft of data still leaves the owner in possession of that data. Passive information attack is thus more dangerous than stealing of goods, as information theft may go unnoticed by the owner.
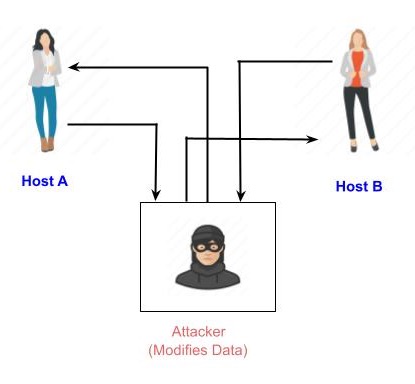
Active Attacks
An active attack involves changing the information in some way by conducting some process on the information. For example,
Modifying the information in an unauthorized manner.
Initiating unintended or unauthorized transmission of information.
Alteration of authentication data such as originator name or timestamp associated with information
Unauthorized deletion of data.
Denial of access to information for legitimate users (denial of service).
Cryptography provides many tools and techniques for implementing cryptosystems capable of preventing most of the attacks described above.
Assumptions of Attacker
Let us see the prevailing environment around cryptosystems followed by the types of attacks employed to break these systems −
Environment around Cryptosystem
While considering possible attacks on the cryptosystem, it is necessary to know the cryptosystems environment. The attacker’s assumptions and knowledge about the environment decides his capabilities.
In cryptography, the following three assumptions are made about the security environment and attacker’s capabilities.
Details of the Encryption Scheme
The design of a cryptosystem is based on the following two cryptography algorithms −
Public Algorithms − With this option, all the details of the algorithm are in the public domain, known to everyone.
Proprietary algorithms − The details of the algorithm are only known by the system designers and users.
In case of proprietary algorithms, security is ensured through obscurity. Private algorithms may not be the strongest algorithms as they are developed in-house and may not be extensively investigated for weakness.
Secondly, they allow communication among closed group only. Hence they are not suitable for modern communication where people communicate with large number of known or unknown entities. Also, according to Kerckhoff’s principle, the algorithm is preferred to be public with strength of encryption lying in the key.
Thus, the first assumption about security environment is that the encryption algorithm is known to the attacker.
Availability of Ciphertext
We know that once the plaintext is encrypted into ciphertext, it is put on unsecure public channel (say email) for transmission. Thus, the attacker can obviously assume that it has access to the ciphertext generated by the cryptosystem.
Availability of Plaintext and Ciphertext
This assumption is not as obvious as other. However, there may be situations where an attacker can have access to plaintext and corresponding ciphertext. Some such possible circumstances are −
The attacker influences the sender to convert plaintext of his choice and obtains the ciphertext.
The receiver may divulge the plaintext to the attacker inadvertently. The attacker has access to corresponding ciphertext gathered from open channel.
In a public-key cryptosystem, the encryption key is in open domain and is known to any potential attacker. Using this key, he can generate pairs of corresponding plaintexts and ciphertexts.
Cryptographic Attacks
The basic intention of an attacker is to break a cryptosystem and to find the plaintext from the ciphertext. To obtain the plaintext, the attacker only needs to find out the secret decryption key, as the algorithm is already in public domain.
Hence, he applies maximum effort towards finding out the secret key used in the cryptosystem. Once the attacker is able to determine the key, the attacked system is considered as broken or compromised.
Based on the methodology used, attacks on cryptosystems are categorized as follows −
Ciphertext Only Attacks (COA) − In this method, the attacker has access to a set of ciphertext(s). He does not have access to corresponding plaintext. COA is said to be successful when the corresponding plaintext can be determined from a given set of ciphertext. Occasionally, the encryption key can be determined from this attack. Modern cryptosystems are guarded against ciphertext-only attacks.
Known Plaintext Attack (KPA) − In this method, the attacker knows the plaintext for some parts of the ciphertext. The task is to decrypt the rest of the ciphertext using this information. This may be done by determining the key or via some other method. The best example of this attack is linear cryptanalysis against block ciphers.
Chosen Plaintext Attack (CPA) − In this method, the attacker has the text of his choice encrypted. So he has the ciphertext-plaintext pair of his choice. This simplifies his task of determining the encryption key. An example of this attack is differential cryptanalysis applied against block ciphers as well as hash functions. A popular public key cryptosystem, RSA is also vulnerable to chosen-plaintext attacks.
Dictionary Attack − This attack has many variants, all of which involve compiling a ‘dictionary’. In simplest method of this attack, attacker builds a dictionary of ciphertexts and corresponding plaintexts that he has learnt over a period of time. In future, when an attacker gets the ciphertext, he refers the dictionary to find the corresponding plaintext.
Brute Force Attack (BFA) − In this method, the attacker tries to determine the key by attempting all possible keys. If the key is 8 bits long, then the number of possible keys is 28 = 256. The attacker knows the ciphertext and the algorithm, now he attempts all the 256 keys one by one for decryption. The time to complete the attack would be very high if the key is long.
Birthday Attack − This attack is a variant of brute-force technique. It is used against the cryptographic hash function. When students in a class are asked about their birthdays, the answer is one of the possible 365 dates. Let us assume the first student's birthdate is 3rd Aug. Then to find the next student whose birthdate is 3rd Aug, we need to enquire 1.25*√365 ≈ 25 students.
Similarly, if the hash function produces 64 bit hash values, the possible hash values are 1.8x1019. By repeatedly evaluating the function for different inputs, the same output is expected to be obtained after about 5.1x109 random inputs.
If the attacker is able to find two different inputs that give the same hash value, it is a collision and that hash function is said to be broken.
Man in Middle Attack (MIM) − The targets of this attack are mostly public key cryptosystems where key exchange is involved before communication takes place.
Host A wants to communicate to host B, hence requests public key of B.
An attacker intercepts this request and sends his public key instead.
Thus, whatever host A sends to host B, the attacker is able to read.
In order to maintain communication, the attacker re-encrypts the data after reading with his public key and sends to B.
The attacker sends his public key as A’s public key so that Btakes it as if it is taking it from A.
Side Channel Attack (SCA) − This type of attack is not against any particular type of cryptosystem or algorithm. Instead, it is launched to exploit the weakness in physical implementation of the cryptosystem.
Timing Attacks − They exploit the fact that different computations take different times to compute on processor. By measuring such timings, it is be possible to know about a particular computation the processor is carrying out. For example, if the encryption takes a longer time, it indicates that the secret key is long.
Power Analysis Attacks − These attacks are similar to timing attacks except that the amount of power consumption is used to obtain information about the nature of the underlying computations.
Fault analysis Attacks − In these attacks, errors are induced in the cryptosystem and the attacker studies the resulting output for useful information.